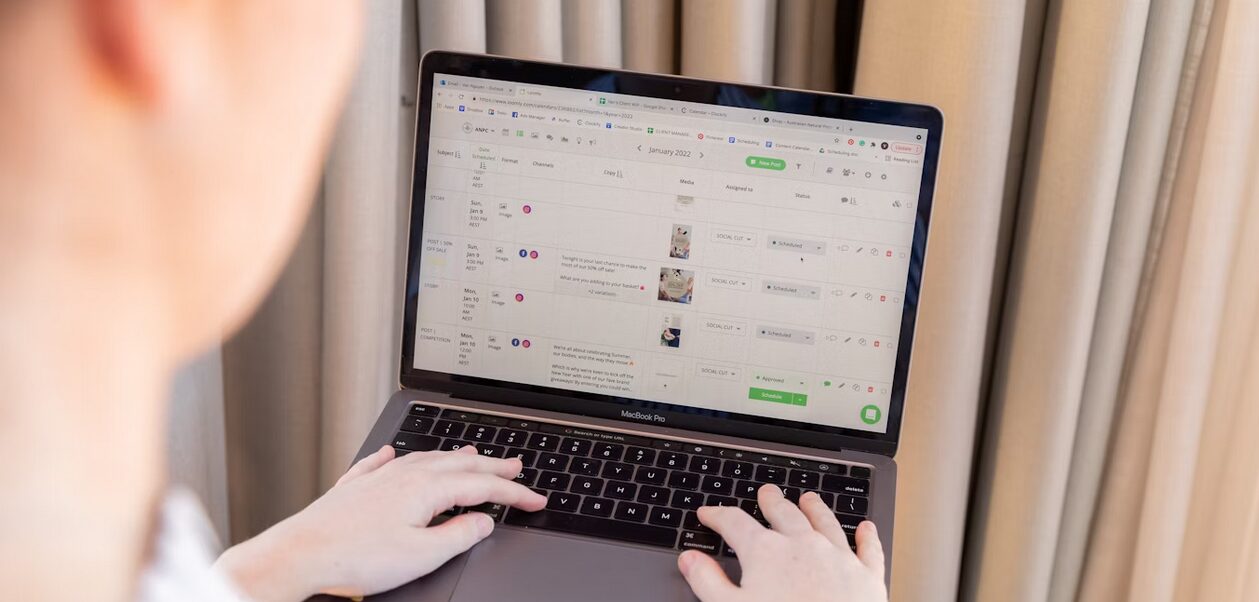
TikTok has become a powerhouse platform for creators, brands, and influencers alike. Many users are seeking methods to increase their visibility, interaction, and overall reach. Among the strategies explored, automation tools such as engagement bots have grown popular. Bots can like, comment, and follow on your behalf, offering an initial boost to videos. However, while automation may seem tempting, careless use can harm an account’s credibility or even lead to penalties. To navigate safely, it’s important to know the best sites to buy TikTok comments and how to combine automation without risking performance. Missteps in using bots are common, but understanding what to avoid can protect both reach and reputation.
Over-Automating Interactions
One of the most frequent errors creators make is over-automation. Using bots to excessively like, comment, or follow accounts can make your engagement appear unnatural. TikTok’s algorithm is designed to detect irregular activity patterns, and sudden bursts of automated interactions can trigger restrictions. Instead of relying entirely on bots, combine them with manual engagement. Respond to real comments, join trending discussions, and interact with niche communities to maintain an organic presence. Moderation is crucial; automation should supplement, not replace, authentic participation.
Ignoring Comment Quality

Many users assume that any comment generated by a bot will suffice, but low-quality or generic messages can backfire. Comments that are irrelevant, repetitive, or out of context not only reduce credibility but may also discourage genuine interactions. Opt for bots that allow configurable, context-appropriate comments or consider platforms that deliver carefully crafted engagement. Proper comment quality encourages conversation and makes your account appear more legitimate to followers and the algorithm alike. Blindly deploying bots without attention to detail can undermine your growth rather than accelerate it.
Neglecting Account Safety
Account safety is often overlooked when using bots. Bots that require your login credentials or connect through unverified platforms can compromise security. Using unreliable services can lead to hacks, unauthorized activity, or permanent suspension. Always choose trustworthy solutions and keep sensitive information private. It’s also wise to monitor account behavior regularly and revoke access to tools that display unusual or suspicious activity. Maintaining account safety preserves your long-term engagement potential and protects personal or brand integrity.
Ignoring Platform Rules and Guidelines

TikTok has clear community guidelines and terms of service, which prohibit certain automated activities. Ignoring these rules can result in shadowbans, reduced visibility, or even account termination. A common misstep is assuming bots are invisible to the system; in reality, algorithms are sophisticated and monitor patterns of inauthentic engagement. Stay informed about TikTok’s policy updates, limit the frequency of automated actions, and integrate organic engagement strategies. Understanding rules is essential for safe and sustainable growth while using automation tools.
Failing to Monitor and Adjust Bot Usage
Many creators deploy bots and forget to track their performance. Failing to monitor automated activity can lead to ineffective strategies or overexposure. It’s crucial to analyze results, adjust settings, and pause bot actions if needed. Regular evaluation ensures that automated engagement contributes positively to growth without triggering penalties. Using analytics tools to track video performance, comment rates, and follower interactions allows for a balanced approach that blends automation with human oversight. Continuous adjustment ensures bots complement your overall TikTok strategy rather than hinder it.
Using bots for TikTok engagement can be a useful tool when approached carefully. …
Read More








 Rooting an Android device is very similar to jailbreaking the iPhone. Rooting gives you superuser access to the Android platform. Rooting your phone means that you can take overall control of the phone and change the original operating system. A program called “SU” (switch user) is installed on the phone and gives you root access to all programs. SU does it by exploiting security holes in the operating system code and device drivers. Rooting is indeed not approvable by manufacturers. Thus, if you do not want to do it, you can still enjoy more modified apps through
Rooting an Android device is very similar to jailbreaking the iPhone. Rooting gives you superuser access to the Android platform. Rooting your phone means that you can take overall control of the phone and change the original operating system. A program called “SU” (switch user) is installed on the phone and gives you root access to all programs. SU does it by exploiting security holes in the operating system code and device drivers. Rooting is indeed not approvable by manufacturers. Thus, if you do not want to do it, you can still enjoy more modified apps through  You can customize your Android devices to run any operating system and to meet your specific needs. It does so because Rooting gives you overall control of your Android device. You can edit system files, change boot images and even remove unwanted apps. For example, there are more than 20 custom operating systems for HTC Desire. These operating systems can let you save apps to your SD card. Besides, it enables you to add Arabic support or remove SenseUI altogether.
You can customize your Android devices to run any operating system and to meet your specific needs. It does so because Rooting gives you overall control of your Android device. You can edit system files, change boot images and even remove unwanted apps. For example, there are more than 20 custom operating systems for HTC Desire. These operating systems can let you save apps to your SD card. Besides, it enables you to add Arabic support or remove SenseUI altogether.

 The Virtual Private Network (VPN) is one of the best solutions to access many other country servers. It is a secure gateway that can guarantee your online data transfer locked in private. It means that you can access everything you do online free of control. When you use a VPN, you get the shadow IP address that lets you browse your Facebook or Twitter account without getting anyone, neither government authorities nor hackers, sniffing around and trying to catch you online. Therefore, it is a safe way to access websites that are banned in China.
The Virtual Private Network (VPN) is one of the best solutions to access many other country servers. It is a secure gateway that can guarantee your online data transfer locked in private. It means that you can access everything you do online free of control. When you use a VPN, you get the shadow IP address that lets you browse your Facebook or Twitter account without getting anyone, neither government authorities nor hackers, sniffing around and trying to catch you online. Therefore, it is a safe way to access websites that are banned in China. Using a proxy can be one of the ways to access social media in China. It uses other websites as a door to get through to Facebook or Twitter. The perfect portrayal is when you are in a movie theater. After entering the hallway, you buy tickets for the movie you want and watch it. Proxies have a similar concept with a fascinating idea. Suppose you start a proxy website in any country and visit social media through it. In that case, the internet data makes it look like you are getting social media in that particular country. As you are in China, you can access any social media you want using the United States proxy. However, this path is not that dependable because a proxy cannot manage social media sites in most cases. Also, the Chinese government often inspect and block proxies.
Using a proxy can be one of the ways to access social media in China. It uses other websites as a door to get through to Facebook or Twitter. The perfect portrayal is when you are in a movie theater. After entering the hallway, you buy tickets for the movie you want and watch it. Proxies have a similar concept with a fascinating idea. Suppose you start a proxy website in any country and visit social media through it. In that case, the internet data makes it look like you are getting social media in that particular country. As you are in China, you can access any social media you want using the United States proxy. However, this path is not that dependable because a proxy cannot manage social media sites in most cases. Also, the Chinese government often inspect and block proxies.

 The Items
The Items





 The collars are divided within the DSLR. They are compact, ultra-compact, semi-professional, or enthusiastic. The types and models are made by manufacturers to capture a large slice of the market. Ultra-compact cameras are made in such a way that they are perhaps the most suitable, usually only fit inside pockets, and are used as earrings, which were indispensable. However, DSLR cameras are probably the highest quality equipment for professionals with the widest range of options, such as external flash, lenses, and tripods.
The collars are divided within the DSLR. They are compact, ultra-compact, semi-professional, or enthusiastic. The types and models are made by manufacturers to capture a large slice of the market. Ultra-compact cameras are made in such a way that they are perhaps the most suitable, usually only fit inside pockets, and are used as earrings, which were indispensable. However, DSLR cameras are probably the highest quality equipment for professionals with the widest range of options, such as external flash, lenses, and tripods. Zoom is just another point with cameras, and there are two types of lens zoom in addition to optical zoom. The aspect is where the light that is what is in the distance must appear larger and closer to the image you are going to follow. Since many camera manufacturers have saved money on photography, this is crucial to their choice. Storage space sizes can vary from 8 MB cards/sticks, which can hold about a dozen mp photos, to larger cards/sticks of 32 GB and …
Zoom is just another point with cameras, and there are two types of lens zoom in addition to optical zoom. The aspect is where the light that is what is in the distance must appear larger and closer to the image you are going to follow. Since many camera manufacturers have saved money on photography, this is crucial to their choice. Storage space sizes can vary from 8 MB cards/sticks, which can hold about a dozen mp photos, to larger cards/sticks of 32 GB and …
 Few games also allow someone to keep their progress after a very short registration, which can be registered through social networking sites. A study that one in five gamers access online games sites. This number has been found to grow over time as game developers are incredibly focused on creating advanced, fan-centric online games that keep a person active even today. There are not many, but the benefits of which many are not aware, although some individuals are against the nature of net games, keep that in mind.
Few games also allow someone to keep their progress after a very short registration, which can be registered through social networking sites. A study that one in five gamers access online games sites. This number has been found to grow over time as game developers are incredibly focused on creating advanced, fan-centric online games that keep a person active even today. There are not many, but the benefits of which many are not aware, although some individuals are against the nature of net games, keep that in mind. Many women and men are shy when it comes to mixing with gamers finding comfort—interacting with other players around the world. Some online groups are formed in a virtual world is a platform where you can express yourself to the outside world without the individuality, which is promising. Also, individuals can interact with each other throughout the game, which is full of gamers. These people come from different regions around the world. Users can talk to players, and friends can watch them before entering the game if the site asks to be accepted.…
Many women and men are shy when it comes to mixing with gamers finding comfort—interacting with other players around the world. Some online groups are formed in a virtual world is a platform where you can express yourself to the outside world without the individuality, which is promising. Also, individuals can interact with each other throughout the game, which is full of gamers. These people come from different regions around the world. Users can talk to players, and friends can watch them before entering the game if the site asks to be accepted.…

 Wide Range
Wide Range

 Be sure to check with the technicians when you visit the service center. The technicians must have competent training and proper license or have extensive experience in iPhone repair. There is a certificate issued by Apple called ACMT (Apple Accredited Macintosh Technician Certification). It is much better to bring your phone to a service center that has one or more authorized technicians.
Be sure to check with the technicians when you visit the service center. The technicians must have competent training and proper license or have extensive experience in iPhone repair. There is a certificate issued by Apple called ACMT (Apple Accredited Macintosh Technician Certification). It is much better to bring your phone to a service center that has one or more authorized technicians.
